docs
Information Assurance Platform: Computational Verification and Privacy
Abstract
This document explains the computational verification techniques utilised within the Information Assurance Platform (IAP). Computational integrity and privacy (CIP) is predominantely required with regards to off-chain computations, although is not limited to this use case. In such settings a client wants to prove that the result of the computation performed off-chain, in a non-observable manner, is correct. The incentive for performing off-chain computations may be to preserve privacy, but is more commonly for reasons of efficiency. Off-chain computations do not need to be verified by the whole blockchain. In order to verify the correctness of the computation whilst preserving the privacy (i.e. not to reveal information about the computation), techniques such as a zero-knowledge proof can be used. In this document we elaborate on zero-knowledge proofs that are relevant to the IAP. Concretely, we describe a specific type of a zero-knowledge proof i.e. ZK-STARKs — ZK-STARKs are utilised within the IAP to ensure computational verification, integrity and privacy of computations.
Index
- Information Assurance Platform: Computational Verification and Privacy
- Abstract
- Index
- Introduction
- Preliminaries
- Proof of Knowledge Systems
- Interactive Proofs
- Non-deterministic Polynomial Time Proofs (NP)
- Interactive Polynomial Time Proofs (IP)
- Arthur-Merlin Proofs (AM)
- Multi-Prover Interactive Proofs (MIP)
- Non-Interactive Proofs (NIP)
- Probabilistic Checkable Proofs (PCP)
- Probabilistic Checkable Proofs of Proximity (PCPP)
- Interactive Oracle Proofs (IOP)
- Interactive Oracle Proofs of Proximity (IOPP)
- Summarising PoK Systems
- Zero-Knowledge Proofs
- Practical Zero-Knowledge Proofs
- ZK-SNARKs
- ZK-STARKs
- ZK-SHARKs
- Active Research and Development
- Conclusion
- Copyright
- Disclaimer
- References
Introduction
Anonymous transactions were popularized by the Bitcoin blockchain and have recently evolved into sophisticated tools layered with unique flexibility. The Ethereum ledgerA1 capabilities have aided the growth of anonymous transaction products like Zcash, JPMorgan’s Quorum platform, and as of October 2018 Ernst & Young’s EY Ops Chain Public Edition. Zero knowledge proofs are the cryptographic tool enabling each of these products, ensuring the privacy of their respective clients and client transactions. The IAP has partnered with several international organisations (e.g. BDO, EY Global) to collaborate on research and development of next generation applications of such technology.
Zero knowledge proofs (ZKP) are generic constructions that allow one to prove the validity of a statement without leaking any additional information. A ZKP can be used to prove one has a sufficient account balance to support a transaction without revealing the actual balance. ZKPs are also found in digital signatures, secret sharing, electronic voting, and other instances where privacy or anonymity are concerned. A ZKP provides computational integrity while preserving privacy (CIP). The IAP is most concerned with the ability of ZKP to provide transparency while retaining the quality of privacy.
This is of utmost importance in off-chain computations. Off-chain computations improve the efficiency of blockchain computations and save costs associated with a computation. An off-chain computation can be performed on a side or private chain; examples of which are integral to the IAPA2. While this can improve efficiency, it leads to the problem of verifiability of the result of said computations. ZKPs are used to ensure the integrity of the result reported while keeping the off-chain computations private.
Other more practical examples of ZKPs comprise the following: the IAP uses ZKPs to drive one of its four main tools in the Information Assurance Toolbelt (IAT); CyberShieldsA3. EY’s prototype specifically uses ZKPs to verify token exchange between private clients while maintaining consensus. StarkWare, an emerging company with specific interests in ZKPs on blockchains, raised $30M1 in funding as of October 2018. ING Bank announced its Zero Knowledge Range Proof2 solution in Amsterdam at the Enterprise Ethereum Alliance Event. These companies are poised to lead a new wave of technological advancement fueled by ZKPs.
While ZKPs are valuable tools used to ensure statement integrity, the proof sizes can be large in practice. ZK-STARKs are a special category of non-interactive zero knowledge proofs designed so that verification of a proof is succinct. This emerging technology comes as a successor to ZK-SNARKs, another special category of non-interactive ZKPs. The core technology of Zcash is currently based on ZK-SNARKs which provide succinct, non-interactive proofs of knowledge. The ZK-SNARK creators have improved upon the original design principal which includes a trusted set-up phase. The set-up phase could jeopardize the long-term security of ZK-SNARK proofs if secret values used to generate the set-up were ever leaked. To move toward fully trustless applications ZK-STARKs have been developed. ZK-STARKs avoid a trusted set-up phase and are thus considered to be transparent.
In driving its platform for information assurance, cybersecurity and regulatory technology applications, the IAP includes tools that focus on relevant ZKPs; including ZK-STARKs. In this document, we define ZKPs, present a brief history of developments, and illustrate how they will be used in the IAP Network.
Preliminaries
In this section, we present definitions and notations of zero-knowledge proof systems as well as cover the necessary background information of the technologies utilised in zero-knowledge proofs. We state the following definitions for Proof of Knowledge systems (PoK); however, these definitions also hold for Zero-Knowledge Proof systems (ZKP). PoK systems can be seen as a similar type of ZKPs, whereby a ZKP has in some aspects stricter requirements (e.g. the zero-knowledge property).
Definitions and Notations of Zero-Knowledge Proofs
The Involved Parties: Peggy and Victor
There are typically two parties involved in a Proof of Knowledge (PoK) system: a prover (who we will refer to as Peggy) and a verifier (who we further call Victor). Although the reader is welcome to think of Peggy and Victor as people, Peggy and Victor are represented as Turing machines in the context of PoK systems. Note that a Turing machine is solely a mathematical abstraction of a computer. Fortunately, a PoK protocol generally works under both assumptions. Peggy and Victor may also have a specified ‘level’ of power: they may be all-powerful or may be computationally-bounded. By all-powerful the reader can understand an ‘idealistic’ case: a theoretical assumption that there exists no computational limitations (for example, with regards to the number of bits of storage). By computationally-bounded the reader can consider the real-world case: every computational device is in some way bounded by the number of bits it can process or store. These are assumptions over which a specific PoK system is defined.
Making a Statement
Peggy’s objective in a PoK system is to convince Victor that her statement is correct while Victor wants to verify that Peggy’s statement is correct. One statement mentioned previously might be Peggy’s claim that her banking account balance exceeds a particular threshold. A more general example of a statement is: Peggy claims she ‘has knowledge of a value v’. Victor wants to verify if Peggy indeed has knowledge of this value without requiring Peggy to confess v.
Informally, a statement x is ‘something’ that Peggy wants to prove to Victor. With ‘something’ we typically understand a decision problem: if x is ‘true’ then Peggy is able to convince Victor with high probability (formally, Pr(P(x,w) ↔ V(x) → 1) > 0.99). If a statement is true (we may say a statement is valid, correct or good) then the statement is included in a ‘language’ L. The language L contains all ‘similar’ statements y ≠ x, which are defined over a well-defined structure.
To foster a better understanding of the above terms, we may phrase a statement in terms with a natural language (for example, English):
| Natural language | Formal |
|---|---|
| x is an instance of an alphabet ∑ | a ∈ {a,b,c,…,y,z} |
| a word is the collection of some finite elements of ∑ — in sequence | hello |
| ∑* is the set of all words | {‘hello’,’ hola’,’ hallo’, . . . } |
| a language L is defined over ∑* more concretely, L is a subset of ∑* | {‘hello’,’ blockchain’,’ proof’, . . . } [English] |
In software engineering, we are generally interested in solving algorithms. As such, let us represent these definitions in terms of a function: consider the output of a function b=f(a), where a is some secret input, f(a) is some sort of public function and b is a public output — b here is equal to the statement x above. The language L formally defines rules that statements must fulfill in order to be contained in the language. A formalization of the language L which corresponds to the statement “I have knowledge of a secret value whose output under public function f is b” would be: x ∈ L if x=f(a); f() defines the structure for language L.
Statements are associated with a ‘witness’ w (where w ∈ W and W denotes the set of all witnesses for statement x). A witness, in this context, is a piece of information that efficiently allows someone to verify the correctness (i.e. truth) of a statement. For example, if a statement claims “n is the product of two primes n=p*q” (the integer factorisation problem3), then a witness would be one of the prime numbers p or q4.
The input pair of statement and witness (x,w) to a PoK system is used to create a proof string π. Thus, π is associated to the statement x where π acts as a certificate of the statement x. Peggy sends π to Victor, who can then evaluate it and make a decision to either accept the proof π or to reject it.
Peggy has her private input a and wants to compute function b=f(a). She wants to prove to Victor that b is indeed the output of f(a). By utilising a PoK system she makes the statement x (i.e. x ∈ L which is equivalent to b=f(a)) and the PoK system outputs a proof π for a witness w. Peggy can then send π to Victor (either by publicly announcing π or solely distributing π to Victor for verification).
Notions of Proof Systems
Having defined the actors, formally defined a statement, and provided a PoK system overview, we define two notions which are indispensable to proof systems: the properties of completeness and soundness. Further, in PoK systems, the notion of validity extends the notion of soundness.
We always discuss the definition in natural language and then provide a formal definition. To set-up these notions we say a relation R is defined as follows:
A relation R is a tuple (x,w) where the instance x is an element of the language L and the witness w is an element of the set of all witnesses W. Formally, this is stated as: R = {(x,w) : x ∈ L, w ∈ W}.
Definition: Completeness: A PoK system satisfies the completeness property if an honest prover (Peggy) is able to convince an honest verifier (Victor) about the truth of a correct statement x.
Let (x,w) ∈ R. Then Peggy (P), with knowledge of witness w, succeeds to convince Victor (V) about statement x of length n. With probability Pr, it holds that Pr(P(x,w) ↔ V(x) → 1) = c(n). c(n) is typically 1, except otherwise stated.
Definition: Soundness: A PoK system satisfies the soundness property if a malicious prover, Pat, is not able to convince a honest verifier, Victor, about the truth of a false statement x.
Let (x,w) ∈ R. Then Pat (P’), without knowledge of witness w, should not be able to successfully convince Victor about the truth of a statement x’ (x’ denotes a ‘false’ statement — a statement where P’ doesn’t know w or a statement which is not included in the relation x’ ∉ R). As such, it holds that Pr(P’(x’) ↔ V(x’) → 1) ≤ s(n).
Given the previous defintions, in proof systems it is possible to satisfy the properties of completeness and soundness, yet, Peggy may not ‘know’ the witness w. As such, a stronger definition than soundness is the definition of validity. The notion of valitity is defined to prove ‘knowledge’ of a witness.
Definition: Validity: A PoK system satisfies the validity property if the success probability of a ‘knowledge extractor’ (E), in extracting the witness w, being able to interact with a poentially malicous prover, Pat (P’), must be at least as high as Pat (interacting with Victor), being able to convince V about the truth of the statement x.
Let (x,w) ∈ R, w be a witness, W(x) be the set of all witnesses, κ denote the knowledge error and EP(x) denote oracle access of the knowledge extractor with the prover. Then the PoK system satisfies the validity property, if E given access to any prover P’ the following statement holds: Pr(EP’(x) ∈ W(x)) ≥ Pr(P’(x) ↔ V(x’) → 1) - *κ(x).
Computational Complexity Classes
A PoK is typically associated with a computational complexity class. Complexity classes organize computational problems according to their hardness. The hardness of a problem is measured by the resources it takes to solve the problem. We quantify this in terms of time complexity and space complexity, where the former evaluates the execution time of solutions to the problem and the latter evaluates the memory used to solve the problem.
For PoK systems there exist multiple complexity classes. Two prominent classes are P and NP. P stands for polynomial time and includes all problems that are solvable in polynomial time. One may conceptualize a polynomial time algorithm as something a personal computer can process in less than a few hours. NP stands for non-deterministic polynomial time and includes problems that are not solvable in polynomial time but checkable in polynomial time. This means that given a solution to the problem, it can be verified in polynomial time whether the solution is correct or false. Other complexity classes which are applicable to PoK systems include AM (Arthur Merlin), IP (Interactive Polynomial Time), QIP (Quantum Interactive Polynomial Time), MIP (Multiple-Prover Interactive Polynomial Time) and PCP (Probabilistically Checkable Proofs).
Assessing Scalability
The measures of time and space complexity are used to assess the efficiency and scalability of the prover and the verifier of PoK systems. The time complexity evaluates the amount of time it takes to run an algorithm. Factors that influence the time complexity of a protocol are:
(a) the number of rounds of the protocol, and (b) the size of the inputs.
The space complexity evaluates the amount of memory used by the algorithm. Factors that contribute to the space complexity of a protocol are:
(a) the number of messages sent throughout a protocol, and (b) the length of the messages.
Via these measures, it can be assessed how ‘scalable’ a systems is. Scalability enables us to understand whether a compuational problem can be solved or checked within given time and/or memory contraints.
Modes of Operations
In a PoK system Peggy exchanges messages with Victor in order to convince Victor about a statement Peggy made. Such a message exchange follows either in an interactive or non-interactive fashion.
Interactive Proofs: In an interactive protocol, Peggy and Victor exchange messages over k rounds. After the k rounds Victor either accepts or rejects the proof.
Non-interactive Proofs: In a non-interactive protocol, Peggy sends one message to Victor. Victor evaluates and either accepts or rejects the proof. We emphasize that Victor does not send messages to Peggy.
In the soundness property we have already indicated that Peggy must know a witness w in order to create a valid statement. If Peggy knows w she should be able to convince Victor that the statement is true and convince Victor to accept the proof. The phrase ‘knows’ in this context maps to the second part of a PoK. These proofs can be further refined according to the power or strength of a prover into the following two cases:
Proof of Knowledge (PoK): In a ‘proof’ of knowledge, we assume that Peggy is all-powerful. This means that Peggy is not computationally restricted in any of her executions.
Arguments of Knowledge (ARG): In an ‘argument’ of knowledge, we assume that Peggy is computationally bounded. As such, there is a limit in either time and/or memory complexity which she can’t exceed in order to convince Victor about the truth of her statement x.
Cryptographic Definitions
Zero-knowledge proofs offer computational5 integrity while preserving privacy. To this end, we haven’t defined the terms ‘integrity’ and ‘privacy’ so far. The following two definitions clarify the terms.
Definition: Integrity: A system provides integrity if any unauthorised modification can be detected. Consider a transcript being transferred from Peggy to Victor. A system is integrity-preserving if the transcript is the same after being transferred over an untrusted channel. Typically such checking involves ‘generate’ and ‘verify’ algorithms. The generate algorithm creates a transcript and a certificate of integrity. The verify algorithm takes the transferred transcript with the certificate and accepts if the transcript is the same or rejects if not. Hash functions are typically used to create such a proof of integrity.
Definition: Privacy: A system provides privacy if it does not leak information to any unintended participant. In the context of ZKPs, the proof certificate 𝜋 should not leak any information about the witness w.
Adversarial Model
In PoK/ZKP systems we consider the following adversaries:
- a malicious prover
- a malicious verifier
- an interested outsider.
In the case an entity behaves honestly we assume that entity follows the given zero-knowledge protocol and sends legitimate messages. A malicious entity may deviate from the protocol to send falsified messages in order to ‘break’ the protocol and learn any additional information as a result. We assume that both Peggy and Victor have the incentive to complete the protocol; Victor either accepts or rejects the proof. We exclude denial of service attacks from the attack surface6.
In the case of a malicious prover we consider that Pat wants to convince an honest Victor about a false statement. A ZKP prevents Pat from successfully convincing Victor following the soundness property.
In the case of a malicious verifier we consider that Vanna wants to extract knowledge about the witness w from honest Peggy. Depending on the zero-knowledge protocol, Vanna is able to send challenges to Peggy and learn from the response of her queries. Strictly following a secure zero-knowledge protocol prevents such a case following the zero-knowledge property.
In the case of an interested observer of the communication between Victor and Peggy the observer may learn information from the interaction. The observer may read or alter a message. Reading messages sent between Peggy and Victor should not reveal sensitive information to the observer following a secure zero-knowledge protocol (zero-knowledge property). If the observer alters the message the protocol may fail or Victor may reject the proof. It is therefore important that during the exchange, participants digitally sign their message in order to ensure integrity and authenticity of the messages. Digitally signing a message with an user-specific private key also solves the problem of impersonation attacks (the associated public key can be used to verify the signature of the messages). A special case of alteration attacks is when an observer deletes a message, known as a denial of service attack. If Peggy or Victor detects that a message didn’t arrive after a given time, she/he could either try to resend it or both parties change the communication channel (which the observer hopefully can not alter). An external observer may reuse or replay an old message (or parts or a message) from a successful result of the protocol execution. To prevent such cases some sort of freshness guarantee must be added to the messages. This could be either a timestamp, a counter or a cryptographic nonce.
We exclude any type of side-channel attacks from our threat model where the adversary has access to the computational machines of Peggy or Victor. We assume that both Peggy and Victor are running their protocols on secure and trusted machines. We assume that Peggy and Victor are following the zero-knowledge protocol and have no incentive7 to do otherwise.
Hash functions
Hash functions are used in several zero knowledge protocols, including ZK-SNARKs and ZK-STARKs.
Definition: Hash function: A hash function maps bit strings of arbitrary length to fixed-length outputs. More formally, for a function H : {0,1}* → {0,1}n for finite n, we say H is a hash function.
The flexible input size to hash functions makes them useful for constructing digital signatures, ZKPs, and other algorithms. For use in secure protocols, cryptographic hash functions must always be one-way.
Definition: One-way function: Given b in the image space of H, it must be infeasible to recover an input string a that satisfies H(a)=b.
If the image space of a hash function H is smaller than the size of the domain, then H may also be considered a compression function. In this case it is expected that several such a exist to satisfy H(a)=b .
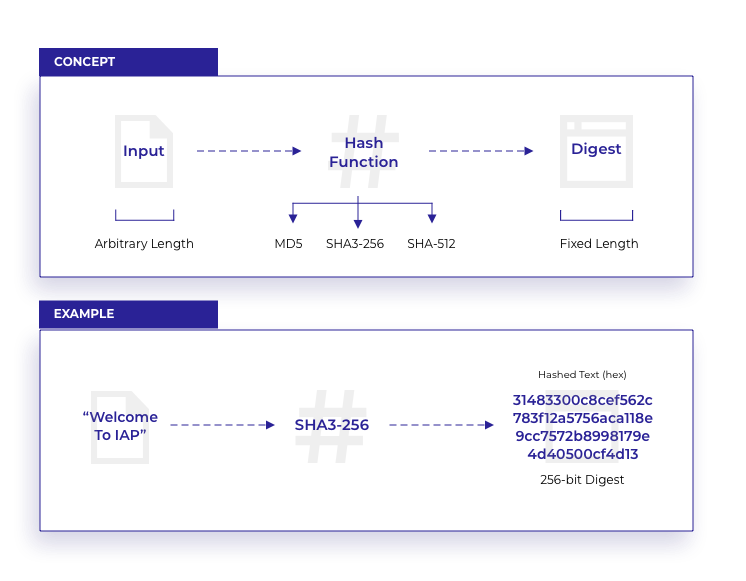
Additional security definitions imposed on hash functions are preimage resistance, second-preimage resistance, and collision resistance. We outline the definitions below.
Definition. Preimage resistance: Given y an element in the image space of H, it is infeasible to find a preimage a such that H(a)=y.
Definition. Second-preimage resistance: Given a, it is infeasible to find a second pre-image b such that H(a)=H(b).
Definition. Collision resistance: It is infeasible to find a,b with a ≠ b,such that H(a)=H(b).
In the context of advanced ZKPs, we are particularly interested in the last property of collision resistance. Collision resistant hash functions like SHA-2 and SHA-3 are believed to be post-quantum secure (meaning that they withstand attacks by a quantum computer). Collision resistance also implies second-preimage resistanceA33.
Elliptic Curves and Pairings
Elliptic Curves and Pairings are essential parts of ZK-SNARKs, a special kind of ZKP discussed below. An elliptic curve is an algebraic structure defined by a curve equation y2 = x3 + Ax + B over a field: e.g. the real numbers, the complex numbers, the rational numbers, or a finite field Fp. Elliptic curve cryptography (ECC) defines curves over finite fields. The points (x,y) over the field which satisfy the curve equation, combined with the point at infinity form the elliptic curve. The point at infinity is added to ensure the set of elliptic curve points form an additive group under a special group law8,9,A30 . For an elliptic curve C defined over finite field Fp, let C(Fp) denote the group formed by the points of CA30.
Suppose for now that the size of C(Fp) is a prime number r ≠ p. In this case, C(Fp) is almost cyclic since any element besides the point at infinity generates the whole group. The smallest integer k such that r ∣ pk - 1 is known as the embedding degree of C. Let us denote the group C(Fp) by G1. The multiplicative group of extension field Fpk contains a subgroup of order r which we denote by GT. The elliptic curve with points from this extension field C(Fpk) also forms a group and this group contains G1. C(Fpk) contains another subgroup of order r which we may call G2.
Definition: Tate pairing: Let g, h be generators of G1, G2 respectively. There exists a map called a Tate pairing that maps G1, G2 to GT such that:
- Tate maps the generators g,h to a generator g of GT
- For field elements a,b Tate preserves the following equality Tate(ag,bh)=gab.
Zcash10, one real-world implementation that uses ZK-SNARKs, digresses to introduce a term called homomorphic hiding in their blog series11, not found in the scientific literature, but which captures an essential concept. Homomorphic hiding is the simplest form of homomorphic encryption, and is a function H() which satisfies:
- Given H(x), H(y), one can compute an algebraic combination, e.g. H(x+y), H(xy), etc.
- H(x) is easy to compute.
- Given H(x) it is difficult to recover x, for most x.
Let Zp denote the finite field of p elements: {0,1,…,p-1} and Zp* the corresponding multiplicative group Zp∖{0}. The group Zp* is cyclic and thus can be generated by some element g ∈ Zp*. Then the HH properties are satisfied by the function H(x) = g^{x mod p-1}, where <g>=Zp* and is illustrated as follows:
- H(x)H(y) = g^{x mod p-1} g^{y mod p-1} = g^{x+y mod p-1} = H(x+y)
- Modular exponentiation is efficiently computable.
- Given g, gx it is difficult, given only classical computational power, to recover input x for most x. This is known as the discrete logarithm problem.
The above Tate pairing construction allows us to generate a HH that preserves addition and multiplication, but first we define three functions:
- E1(x) = x · g
- E2(x) = x · h
- E(x) = x · g
where x · g denotes adding the elliptic curve point g to itself x times, or scalar multiplication. Given two values E1(x), E2(y), one can compute E(xy) using the Tate pairing.
Quadratic Arithmetic Program
One ingredient of ZK-SNARKs that adds to their efficiency is an Quadratic Arithmetic Program (QAP). A technique emerged in 1992 for translating PoK statements to polynomials for interactive proof systems. In 2013 it was shown how to extend this concept in a non-interactive way by using QAPs.
Arithmetic circuits are a collection of gates and wires used to connect the gates such that for a finite input set the circuit will perform a computation and produce an output. To construct a QAP from a given PoK statement the statement is first converted into an arithmetic circuit. The circuit’s multiplication gates must have exactly two input wires: one left and one right, to be converted to a QAP. These help to define a legal assignment for the circuit; a set of input wires and output wires that are the result of a multiplication between exactly two wires.
In the QAP each multiplication gate is associated with a field element called a target point. The left and right input wires correspond to left and right polynomials. The output of each multiplication corresponds to an output wire polynomial. The left and right polynomials are defined to be zero on all target points except the ones to which they correspond. The legal assignment elements are coefficients of the left, right, and output polynomials. This construction is carefully designed so that a legal assignment is valid if and only if the polynomial P = LR-O is zero for all the target points12.
Homomorphic Encryption
Fully homomorphic encryption (FHE), hailed by some as the “Holy Grail” of cryptography13,A32 has revolutionized digital privacy in some trustless applications. This primitive ensures that data encrypted in a particular way can be processed without access to the secret decryption key. The result of decrypting first then running some computation, C, on plaintext will yield the same result as running C on ciphertext and then decrypting. FHE allows ciphertext data to be manipulated, queried, and operated on without compromising the privacy of the underlying plaintext; removing the need for trust. An untrusted server or third-party may then compute on user encrypted data and return the encrypted results of the query or operation to the users who then use their own private key to decrypt the results.
The first FHE scheme was proposed in 2009A25, and improvements made in 2011 still yielded implementation results with public keys exceeding 2GBA26. Several homomorphic encryption libraries exist14 and although FHE is still under development the significance of this cryptographic primitive will fundamentally change cloud computing and storage. It also holds promise in such advanced areas as unlocking the relationships between DNA sequencing and disease.
IAP Network is currently incorporating homomorphic encryption libraries into the base library of the open source IAP Client, extending the verification capabilities of the IAT15 CyberShield tool. These privacy preserving abilities of homomorphic encryption allow non-trusted parties to perform computations on sensitive data without the ability to view the plaintext data. This will be extended to FHE once libraries become available.
Database security includes encrypting stored data16. The queries to databases can leak information about the corresponding plaintext data and should also be secured. Queries by a lawyer for past cases involving workplace misconduct or other controversial topics might reveal sensitive information about a client. Queries by an employee about job openings might reveal the intention to leave his current employer. The ideal scenario is for a user to encrypt her queries, send the encrypted queries to the server and receive encrypted results from the server. When she is ready she can decrypt the results which are the response to her plaintext query.
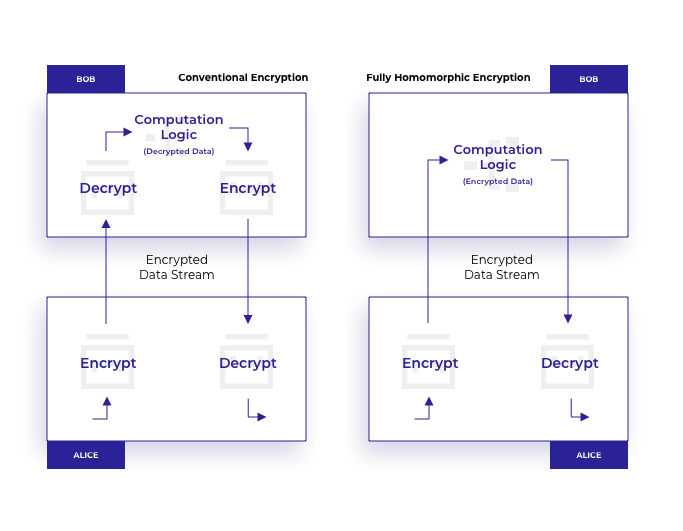
Suppose users allow financial holdings to be monitored in real-time by third-party services. These services might include alerts about suspicious activity, predictions based on spending habits, and forecasts for expected future balances. These services are currently provided by trusted parties. Fully homomorphic encryption would allow user financial data to remain encrypted while being analyzed by such business entities.
IAP Network is actively researching additional use cases for FHE with regards to the IAT. FHE has been shown in the literature to provide theoretical solutions for achieving verifiable computation on private dataA24. This is especially useful for outsourced and cloud computations. CyberTraces and CyberShields are two components of the IAT that offer independently verifiable evidence events. FHE-based verifiable computation would enhance CyberTraces and CyberShields by adding to the variety of security models and assumptions.
One of the most interesting implications of FHE is the opportunity for scientists to study DNA sequencing in a privacy-preserving manner. Genome analysis seeks to study genetic information to identify genetic predispositions and in doing so prevent fatal conditions. Though this line of research offers promising benefits to patients, genetic information is and must remain confidential. Researchers are pursuing FHE as a solution. Since 2014 the annual iDASH Privacy & Security Workshop has sought to address biomedical challenges involving big data.
IAP Network continues to monitor the progress relating to FHE and the analysis tools emerging from the iDASH workshop series. These state-of-the-art techniques may readily extend to identity management and privacy, a major use case of the IAP, by better detecting fraudulent activity based on private user history. Other sensitive data like private votes may be protected; ensuring accurate government polling of electorates. The tallying of private votes can be displayed using CyberChainsA8 to maximize transparency.
Proof of Knowledge Systems
The following section provides an overview of current Proof of Knowledge (PoK) systems. A PoK can be seen as something similar, yet separate to a zero-knowledge proof (ZKP). PoKs have the similar properties as ZKPs in terms of completeness and soundness, but PoKs typically include an extractability property in contrast to the zero-knowledge property of a ZKP. The following presents a theoretical overview of PoK systems, followed by an overview of ZKP systems. Further, in the Practical Zero-Knowledge Proofs section we present an overview of practical implementations of zero-knowledge proofs.
Interactive Proofs
The first class of PoK systems in the IAP are so called interactive proof (IP) systems. IP systems are by far one of the biggest class of proof systems and include multiple specialisations (explained further below in this section). In an IP system the prover and the verifier engage in an interactive protocol; messages are exchanged between both entities, and at a given point in time the verifier accepts or rejects the proof.
Non-deterministic Polynomial Time Proofs (NP)
Interactive proofs pertaining to the class of NP are the simplest form of interactive proofs. These proofs are single-round interactive proofs. We can barely say that such proofs are interactive; they follow the same principles as interactive proofs, yet run in a single round. For simplicity, we say proofs in this category are IP[1] proofs; the ‘1’ denotes a single round. Following the character convention introduced in our recap, there exist an all-powerful prover (Peggy) and a computationally-bounded verifier (Victor). Being all-powerful, we understand that Peggy is not limited by any computational resources such as memory space or computation time. Peggy is considered to be a type of ‘idealistic’ entity17. Victor is represented by a deterministic18 polynomial-time machine19.
For any problem in the complexity class NP a proof protocol follows:
- Peggy looks at the input a, computes b=f(a) and gives Victor a proof π associated with the computation, where π proves that b is indeed the result of f(a).
- Victor verifies π in polynomial time and if π is valid he accepts, otherwise rejects the proof.
Interactive Polynomial Time Proofs (IP)
Interactive proofs pertaining to the class of IP extend the NP proof class by allowing the protocol to run over multiple rounds. Multiple messages may be exchanged between Peggy and Victor before Victor reviews the proof π and makes a decision to accept or reject the proof. To indicate the number of rounds in the class we denote the class as IP[k], where k is the number of rounds.
Victor has access to a string of random bits whose length is polynomial in the size of the input statement x. The random choices of Victor are kept private. Such a protocol is further referred to as a private coin protocol. Peggy and Victor exchange a polynomial number of messages (i.e. the length of all messages over k rounds are bounded by that polynomial). For any problem in the complexity class IP[k] a proof protocol follows. The protocol runs over two stages; an interaction phase where Peggy and Victor are exchanging messages and a decision phase where Victor makes a decision to either accept or reject the proof.
Interaction Phase:
1 - k: Peggy and Victor exchange messages.
Decision Phase:
- If the statement is valid, i.e. x ∈ L, then Victor accepts the proof π with probability ≥ ⅔.
- If the statement is invalid, i.e. x ∉ L, then Victor rejects the proof π with probability ≤ ⅓.
Arthur-Merlin Proofs (AM)
Interactive proofs pertaining to the class of AM extend the IP proof class by allowing Peggy to learn the random choices (i.e. random bits) of Victor. In comparison to IP where all random choices of Victor are private, in AM proofs the random bits of Arthur are public. We denote the all-powerful prover as Merlin and the verifier as Arthur. Due to the public randomness choices, AM proofs are referred to as public coin protocols. Other than the public randomness of Arthur, AM proofs follow the same conventions as IP proofs20.
Multi-Prover Interactive Proofs (MIP)
Interactive proofs pertaining to the class of MIP extend the IP proof class by allowing two independent provers, Peggy and Pat, to convince Victor about the truth of a statement x. It is important to say that Peggy and Pat are independent; they may communicate with each other beforehand, but cannot communicate with each other once Victor starts to send messages to them. The idea of multi-prover interactive proofs is motivated by minimising the probability of a ‘lying’ prover. An analogy can be made of the interrogation of a criminal; it may be easier to detect if a criminal is lying if he and his partner are interrogated in separate rooms (i.e. independence). Adding another prover might reveal ‘more’ or ‘different’ details (or viewpoints) of a story (i.e. a statement x).
Non-Interactive Proofs (NIP)
The second class of PoK systems we are looking at are the so-called non-interactive proofs. This is a variant of PoK systems in which no interaction between Peggy and Victor is necessary. By ‘no-interaction’ we mean that Peggy sends a message to Victor who then makes a decision based on the information he obtains from Peggy.
To enable a ‘message exchange’ between Peggy and Victor both must share a common reference string which enables computational zero-knowledge without the requirement of interaction. Sharing of a common reference string between both parties follows the common reference string model21; a specific cryptographic model for non-interactive zero-knowledge proofs.
Another way of achieving non-interactive proofs in the random oracle model22 is via the Fiat-Shamir heuristic23. Fiat-Shamir enables the transformation of an interactive PoK to a non-interactive one. The interactive proof must be public coin (ie. the verifiers randomness needs to be public) in order to be convertible to be non-interactive.
Probabilistic Checkable Proofs (PCP)
The next class of PoK systems we are looking at are the so-called probabilistic checkable proofs. Proofs pertaining to the standard class of PCP are verifiable in polynomial time for a set of single-round, non-interactive decision problems. Specialisations in this class allow interactive decision problems24 as well as restrict the query complexity to be linearly bounded25.
One may ask now what is so special about these kind of proofs, since all previous classes discussed before already achieve the same goals. The prominent feature of PCPs is that the verifier Victor has access to only a bounded amount of randomness; we denote such access by r(n) (where n denotes the length of the random bit string) and further refer to it as randomness complexity. Victor only reads a bounded amount of bits from the proof π; we denote this by q(n) and further refer to it as query complexity.
In addition to the existing notations we denote with c(n) the completeness probability: c(n) gives a lower bound to which a proof achieves the completeness property (i.e. Peggy convinces Victor about the truth of a statement). With s(n) we denote the soundness probability: s(n) gives an upper bound to which a proof achieves the soundness property (i.e. a malicious prover, Paul, is able to convince Victor about a false statement).
For any problem in the complexity class PCPc(n),s(n)[r(n),q(n)] a proof protocol follows:
- Peggy looks at the input a, computes b=f(a) and gives Victor a proof π associated with the computation. In this context, π proves that b is indeed the result of f(a).
- Victor verifies π in polynomial time by utilising randomness bounded by r(n) and querying q(n) bits of π:
- If the statement is valid, i.e. x ∈ L, then Victor accepts the proof π with probability at least c(n).
- If the statement is invalid, i.e. x ∉ L, then Victor accepts the proof π with probability at most s(n).
Typically in PCP proofs, unless stated otherwise, c(n) is ≥ 1 (probability that Victor accepts a true π) and s(n) is ≤ ½ (probability that Victor accepts a false π).
Previous authors have shown several relationships between the PCP complexity class with other complexity classes. One of these is the prominent PCP theorem26: PCP[ O(log n), O(1) ] = NP. This theorem states that every decision problem in the NP complexity class has a probabilistic verifiable proof of logarithmic randomness complexity r(n) = O(log n) and constant query complexity q(n) = O(1).
Probabilistic Checkable Interactive Proofs (PCIP)
Generic PCPs are inherently one-round protocols. A interactive extension was first proposed by Kalai and RazA31. In their extension they allow a verifier to have additional oracle access to a PCP before the verifier starts with an IP protocol. This type of protocol combines the flexibility of interactive proofs (allowing Victor to communicate with Peggy over multiple rounds) with the expressiveness of a PCP (allowing a wider range of problems27).
Due to these improvements interactive PCP protocols gained wide attention by the cryptographic community. This resulted in a wide study to improve on the preliminary results of Kalai and Raz; the section below on Interactive Oracle Proofs explains these results in more detail.
Linear Probabilistic Checkable Proofs (LPCP)
Another improvement of generic PCPs is to limit the proof system to be an argument system. As such it only achieves computational soundness, yet improves on the communication and computation time to be linear bounded. This inherently changes the prover Peggy to be computationally bounded (and not all-powerful). As a result of this the proof string π doesn’t need to be polynomial in size. Instead the PCP may be viewed as a linear function.
Probabilistic Checkable Proofs of Proximity (PCPP)
Further extending and improving on proofs of the class PCP is the next class of PoK systems; probabilistic checkable proofs of proximityA29 (PCPP). In a PCPP proof the randomised verifier Victor gains access to a few bits of the proof π, equivalent to a PCP. Victor gets access to only a few bits of input x. Victor is asked to verify if the statement x ∈ L holds. Victor cannot generally be expected to distinguish if x ∈ L from the case that x ∉ L, but should be very ‘close’ to it; Victor is expected to be able to distinguish between these two cases and reject any x (i.e. x∉ L) if x is ‘far’ from L. In natural language; x is nowhere near to being included in the language L.
To cope with these developments we introduce another parameter to the PCPP PoK system: the proximity parameter δ. δ will indicate how ‘far’ a statement x is to be allowed to differ to be included in the language x ∈ L. We say Victor is only reading q’ ≤ q(n) bits from the input statement x.
For any problem in the complexity class PCPPs(n),δ[ r(n),q(n) ] a proof protocol follows:
- Peggy looks at the input a, computes b=f(a) and gives Victor a proof π associated with the computation.
- Victor verifies π in polynomial time by utilising randomness bounded by r(n), querying q(n) bits of π as well as q’ bits of x:
| If the statement x is δ-close to L, i.e. | x ∈ L | ≤ δ, then Victor accepts the proof π with probability at most s(n); otherwise he rejects the proof π. |
A PCPP with proximity parameter δ = 0 is referred to as an exact PCPP, allowing no deviation of x from the language L.
Interactive Oracle Proofs (IOP)
The next class we are looking at was already briefly introduced in the section of PCIPs. Interactive Oracle ProofsA20 (IOPs) combine the features of IPs and PCPs but in a more subtle way than PCIPs. In a PCIP a verifier has additional oracle access to a PCP before the interactive protocol starts.
In an IOP the verifier Victor is not required to read the messages of prover Peggy in their entirety. Victor has oracle access to Peggy’s messages and may probabilistically query those messages. In this context we add another parameter: l will denote the length of the proof π (concretely, l sums up the total number of bits of all messages sent from Peggy to Victor). We further remind the thoughtful reader of the parameters k denoted as the round complexity (in natural language: the number of rounds), c(n) the completeness probability (if not specified otherwise, c(n) is typically assumed to be 1), s(n) the soundness probability and r(n) the randomness complexity (i.e. the number of random bits). Specific to IOP systems, in the i-th round of interaction we say Victor sends message mi to Peggy, who reads the message in full (yes, in full; the mindful reader is reminded that it is Peggy who reads the message in full) and for response messages ni from Peggy to Victor; Victor has oracle access and queries them probabilistically with q(n) (the query complexity), denoting the total number of bits Victor reads from the messages ni.
For any problem in the complexity class IOPc(n),s(n) [ r(n),q(n),k,l ] a proof protocol follows:
Interaction Phase:
1 - k: Peggy and Victor exchange messages (mi, ni).
Decision Phase:
- Victor verifies π in polynomial time by utilising randomness bounded by r(n) and querying q(n) bits of π:
- If the statement is valid, i.e. x ∈ L, then Victor accepts the proof π with probability ≥ c(n).
- If the statement is invalid, i.e. x ∉ L, then Victor rejects the proof π with probability ≤ s(n).
IOPs generalise IPs and PCPs. A PCP is essentially a IOP with k = 1 and the first message from Victor to Peggy is considered to be empty. An IP is a IOP where Victor is querying the whole proof π.
Interactive Oracle Proofs of Proximity (IOPP)
The last class of PoK systems we are looking at extend the previous class by having additional query access to the input statement x (concretely: querying only a few bits of the input). This is similar to the class of PCPP, and is the so-called interactive oracle proofs of proximityA17 (IOPP). We can say that an IOPP merges the classes IOP and PCPP. An IOPP is an IOP where Victor has access to a oracle to query input x. A proximity parameter δ decides if a statement x is included in a language x ∈ L, if x is δ-close to elements of L. This means that Victor accepts proofs π where x is δ-close, otherwise Victor rejects the proof.
Similar to the argument of IOPs (that generalise IPs and PCPs) we can say that IOPPs generalise IOPs and PCPPs. A PCPP is an IOPP with k = 1 (single round); further, a IOP is an IOPP where Victor queries the whole input x.
For any problem in the complexity class IOPPs(n),δ [ r(n),q(n),k,l ] a proof protocol follows:
Interaction Phase:
1 - k: Peggy and Victor exchange messages (mi, ni).
Decision Phase:
- Victor verifies π in polynomial time by utilising randomness bounded by r(n), querying q(n) bits of π as well as q’ bits of x:
-
If the statement x is δ-close to L, i.e. x ∈ L ≤ δ, then Victor accepts the proof π with probability at most s(n). - Otherwise he rejects the proof π.
-
Summarising PoK Systems
There exist a wide variety of PoK systems. Starting with simple proof systems for the class of NP the previously mentioned proof systems continuously add on extra features. Or, in other words, generalise the previous proof systems. In the previous sections we have learned that a PoK system typically consists of two parties: a prover Peggy who wants to convince a verifier Victor about the truth of a statement. In doing so she creates a proof string π which she communicates via a protocol to Victor. Victor then accepts or rejects the proof π.
In Table 1 we present an overview of the previously discussed PoK systems. We use the following notations and parameters:
- # of messages — indicates how many rounds the protocol runs; possible values are : k ∈ N;
- prover complexity — indicates the ‘power’ of Peggy; possible values are: all-powerful or computationally bounded;
- verifier complexity — indicates the ‘power’ of Victor; moreover, we indicate the number of bits read from proof string π either as full or as q(n);
- verifier randomness — indicates the randomness used by Victor; possible values are full or r(n);
- completeness — indicates the probability that Victor accepts the proof π; for proximity proofs we define the ‘proximity’ parameter δ; possible values are: δ, c(n) ∈ [0,1];
- soundness — indicates the probability that Victor rejects the proof π; in other words, the error rate that Victor accepts a false proof π for a statement x ∉ L; possible values are: δ, s(n) ∈ [0,1];
| Parameter | # of messages k | Prover Complexity | Verifier Complexity q(n) | Verifier Randomness r(n) | Completeness* c(n) | Soundness* s(n) | |
|---|---|---|---|---|---|---|---|
| IP | |||||||
| NP | single | all-powerful | full | (private) full | 1 | 0 | |
| (generic) IP | k | all-powerful | full | (private) full | ≥ ⅔ | ≤ ⅓ | |
| MA | single | all-powerful | full | (public)16 full | ≥ ⅔ | ≤ ⅓ | |
| AM | k | all-powerful | full | (public) full | ≥ ⅔ | ≤ ⅓ | |
| MIP | k | collection of non-communicating strategies | full | (private) full | ≥ ⅔ | ≤ ⅓ | |
| NIP | single | all-powerful | full | (public)17 full | c(n) | s(n) | |
| PCP | |||||||
| (generic) PCP | single | all-powerful | q(n) | (private) r(n) | 1 | ≤ ½ | |
| PCIP | k | all-powerful | q(n) | (private) r(n) | 1 | ≤ ½ | |
| LPCP | single | computationally-bounded | q(n) | (private) r(n) | 1 | ≤ ½ | |
| PCPP | single | all-powerful | q(n) | (private) r(n) | δ | 1 - δ | |
| IOP | k | all-powerful | q(n) | (private) r(n) | 1 | s(n) | |
| IOPP | k | all-powerful | q(n) | (private) r(n) | δ | 1 - δ | |
Table 1: Overview of previously discussed proof of knowledge systems. * indicates standard values, unless stated otherwise.
Zero-Knowledge Proofs
Zero knowledge proof systems, originating from a 1985 journal submissionA27, allow one to prove that a statement is true without revealing more than the truth of the statement. A statement such as “893 is a composite number” can easily be proven true by providing one non-trivial factor of 893. This approach reveals more than the truth of the statement and would consequently violate the zero knowledge property. A general zero knowledge proof system is comprised of a statement and some communication exchange between two parties; a prover and a verifier. The prover makes a statement to the verifier and attempts to convince the verifier that the given statement is true.
In graph theory it is known that given two graphs, it is difficult to find a homomorphism between the graphs28. Suppose Peggy knows a homomorphism between two graphs G1,G2, and wants to prove her knowledge to Victor. Suppose further that Peggy does not wish to reveal her homomorphism but still aims to convince Victor that she does know a mapping. A zero-knowledge proof system can help solve Peggy’s problem. Victor challenges Peggy by sending her vertices of G1and requests the image of each vertex under her secret homomorphism. After several rounds of challenges and responses from Peggy, Victor can determine whether the vertex images reported by Peggy respect the properties of a graph homomorphism. Eventually Victor will be convinced that Peggy does know a homomorphism without ever learning what the homomorphism is.
In this scenario Peggy sought to prove the statement “I know a homomorphism between G1,G2.” Statements in zero knowledge proof systems should be easy to verify via a witness. In the case of the integer 893, there are two witnesses; 19 and 47. In Peggy’s case her secret homomorphism is a witness. A witness should not be revealed in a zero knowledge proof, but must be easy to verify. We emphasize that Peggy’s interaction with Victor is classified as an interactive zero knowledge proof. The particular proof systems we discuss later, ZK-SNARKs and ZK-STARKs, do not require nor permit Victor to make queries to Peggy. We classify such systems as non-interactive proofs.
| A statement is formally defined over a language and outputs a proof. The statement “893 is a composite number” can be defined over the language L ={ (n,d) | if d divides n with 1 < d < n, then n is composite}. A proof π should be necessary and sufficient information to convince a verifier that a statement is true. |
While a PoK system fulfills only the properties of completeness and soundness, a zero-knowledge proof additionally has the property of zero-knowledge:
Definition: Zero-Knowledge: A PoK system satisfies the zero-knowledge property if a verifier (Victor) is not able to learn anything else from the proof except that the statement is true or false.
If (x,w) ∈ R then no verifier should be able to infer anything about the witness w except that x is a valid statement of language L and the prover is in the possession of a witness w which can prove that.
Variants of Zero-Knowledge Proofs
Depending on the ‘power’ of both Peggy and Victor different variants of the zero-knowledge property can be achieved. For the definitions below we need to state an assumption — ZK systems assume there exists a simulator accessible to every verifier which is able to ‘simulate’ the interaction between Peggy and Victor. Then, the following variants apply:
Definition: Perfect Zero-Knowledge: a ZK-PoK system achieves perfect zero-knowledge if the distribution between the simulator S and the real interaction between Peggy and Victor remains completely indistinguishable.
Definition: Statistical Zero-Knowledge: a ZK-PoK system achieves statistical zero-knowledge if the distribution between the S and the real interaction between Peggy and Victor is statistically close (i.e. negligible).
Definition: Computational Zero-Knowledge: a ZK-PoK system achieves computational zero-knowledge if the distribution between the S and the real interaction between Peggy and Victor remains indistinguishable by a computationally-bounded algorithm (i.e. polynomial-time Turing machine).
Advanced Zero-Knowledge Proofs
The above overview of a PoK and a natural specialisation as a zero-knowledge proof allow us to now dig deeper into desirable properties of such proof systems. Achieving the basic properties of such systems (i.e. completeness and soundness) can be done fairly efficiently with current state-of-the-art technology. Achieving the zero-knowledge property can be achieved in a similar manner. If more properties are added then the zero-knowledge systems become increasingly complex. To utilise such systems in real-world settings, an application designer must keep certain limitations or trade-offs in mind.
The following lists desirable properties of advanced PoK systems. We will then cover two advanced proof systems: ZK-SNARKs and ZK-STARKs.
(Desirable) Properties of Proof Systems
Definition: Succinctness: A PoK system is succinct if the time to verify the validity of the statement is much smaller than simply recomputing the statement (i.e. the function). The naїve approach to verifying correctness of a statement is to simply recompute the function with the given inputs. This may not always be the optimal solution. For example, if we consider resource intensive operations then it might be too expensive to recompute the original function during the verification step. The property of succinctness is very useful despite coming with the price that while verification time is much smaller, the time to create a proof is larger than simply computing the function.
Definition: Transparency: A PoK system is transparent if any randomness used by the prover or verifier is public. PoKs following such a convention are typically referred to as Arthur-Merlin or Merlin-Arthur proofs. PoK systems which don’t follow these conventions typically rely on a trusted set-up phase. Private randomness is used during this phase to generate certain parameters used for later operations. It is essential that the randomness in this phase doesn’t leak to any malicious entity (i.e. prover, Pat) otherwise Pat may be able to convince Victor about a false statement x’ without Victor being able to identify that there was something amiss within the protocol.
Definition: Universality: A PoK system is universal if it can be applied to any computational problem in its relevant computational complexity class. Goldreich et al.A28 proved that for every problem in the class of NP, there exists a zero-knowledge proof. Being compliant to solve any computational problem typically comes with an efficiency trade-off.
Definition: Scalability: A PoK system is scalable if the prover runs in quasilinear time and verifier validates the proof in polylogarithmic time. Verifier scalability is very important in order to achieve succinct proofs. To be useful in any real-world scenario the prover must also scale when the function complexity (i.e. circuit size29) and the input size (i.e. number of variables) increase.
Definition: Post-Quantum Security: A PoK system is post-quantum secure if it withstands the attacks of a quantum computer. Shor’s algorithm30 presents a quantum polynomial time attack on some public-key cryptography based on the integer factorisation problem and the discrete logarithm problem. Because quantum attacks against collision-resistant hash functions have not been found to run in quantum polynomial time, it is believed that if a PoK system is only based on collision-resistant hash functions then the PoK system remains post-quantum secure.
Practical Zero-Knowledge Proofs
The recent introduction of zero knowledge proofs to a more mainstream audience has initiated efforts to standardize these protocols. The first ZK Proof Standards Workshop31, held in May 2018, was organized to further the development and use of zero knowledge proofs by gathering together field experts from both industry and academia. This first workshop aimed to develop metrics for assessing the security of ZK Proofs and to find the balance between performance and security tradeoffs for practical implementations and applications, among other goals. Whitepapers32 from the workshop proceedings reveal the many factors involved in establishing a secure and practical zero knowledge proof.
The efficiency of a zero knowledge proof is based on the running time of the prover, the running time of the verifier, the memory required to store proofs and witnesses, and the cost of any initialization or set-up phase. We quantify these factors in terms of time complexity and space complexity and further classify zero knowledge proofs into complexity classes.
In practice the statement produced by the prover is converted to a circuit. The size of the proof should be sublinear in the size of the statement circuit to be considered an efficient zero knowledge proof. ZK-STARK constructions convert a statement to a set of polynomials over binary fields that satisfy certain constraints. This process is known as arithmetization.
Different zero knowledge proof techniques arithmetize statements differently. In the Ligero protocolA12 statements are converted to circuits and then to matrix over a finite field, not necessarily binary. In range checking proofs the statement is converted to a set of multivariate polynomials over finite fields. The range checking proofs are not considered quantum-secure as they depend on the intractability of the discrete logarithm problem. These different approaches to statement conversions are being addressed by the ZKProof.org Workshop37 series as well as ideal file formats and compilers.
Existing Libraries and Implementations
ZK-SNARKs have been adopted by the tech community in the form of libraries and implementations. The most prominent library is Libsnark, developed by the SCIPR lab, which offers C++ implementations of all aspects of ZK-SNARKs. IAP Network has implemented the Zcash libsnark library into the IAT CyberShield tool for its proof of concept. Ethsnarks, Zsl-q, and Jsnark offer Ethereum, Quorum, and Java variants, respectively. A general toolbox for ethereum and off-chain zero knowledge is offered in ZoKrates, and an end-to-end toolchain in Pequin. As previously mentioned, ZK-SNARKs require a trusted set-up phase and library Mpc offers a set-up alternative using secure multiparty computation protocols. Distributed ZK-SNARKs are available with Dizk. Additional open-source resources are Bellman, Groth16, and Snarky.
| Library | Description | Reference | |
|---|---|---|---|
| libsnark | de facto library | https://github.com/scipr-lab/libsnark</th> </tr> | |
| ethsnarks | ethereum variant | https://github.com/HarryR/ethsnarks</th> </tr> | |
| zsl-q | JPMorgan Quorum zero knowledge security layer | https://github.com/jpmorganchase/zsl-q</th> </tr> | |
| dizk | distributed zk-snarks | https://github.com/scipr-lab/dizk</th> </tr> | |
| jsnark | java implementation of zk-snarks | https://github.com/akosba/jsnark</th> </tr> | |
| bellman | rust implementation of zk-snarks | https://github.com/zkcrypto/bellman</th> </tr> | |
| groth16 | ZK-SNARK variant by Groth16 | https://github.com/zkcrypto/groth16</th> </tr> | |
| mpc | Secure multi-party protocol for trusted setup phase | https://github.com/QED-it/mpc</th> </tr> | |
| snarky | Library for R1CS SNARKs | https://github.com/o1-labs/snarky</th> </tr> | |
| pequin | End-to-end toolchain for SNARKs | https://github.com/pepper-project/pequin</th> </tr> | |
| ZoKrates | ZK-SNARK toolbox for Ethereum; off-chain | https://github.com/JacobEberhardt/ZoKrates | |
| Library | Description | Reference |
|---|---|---|
| ZK-STARK | ZK-STARK library | https://github.com/elibensasson/libSTARK |
| ING ZKRP | Zero knowledge range proof | https://github.com/ing-bank/zkrangeproof |
| ZKBoo | Quantum-secure zero knowledge proof | https://github.com/Sobuno/ZKBoo |
| Picnic | Post quantum signature | https://github.com/Microsoft/Picnic |
| Picnic | Post quantum signature | https://github.com/IAIK/Picnic |
| Bulletproofs | Library for bulletproofs | https://github.com/bbuenz/BulletProofLib |
| Bulletproofs | Library for bulletproofs | https://github.com/dalek-cryptography/bulletproofs |
| Bulletproofs | Library for bulletproofs | https://github.com/ElementsProject/secp256k1-zkp |
| Use Case | Statement | Private input | Function |
|---|---|---|---|
| Range-checking proofA23 Verifying sufficient credit score |
"Credit score is within the desired range" x ∈ [a,b] |
Yes Credit score |
Public Greater than, less than |
| Set membershipA14 Is a passport number found on a no-fly list |
"Passport number is an element of the no-fly list" x ∈ S |
Yes Passport number |
Public Set intersection |
| Verify computationA11 Verify hash value for blockchain without revealing the input |
"f(x)=y" | Yes Input x |
Public f() |
| Knowledge of committed values, equality of committed values, relationships between committed values | "I know x such that h(x)=y" "I know x1 < x2 such that h(x1)=y1, h(x2)=y2" |
Yes Inputs x,x1,x2 |
Public h |
| Knowledge of a signature on a message/committed value | "This is a valid signature on a private committed value" | Yes Committed value |
Public Signature algorithm |
| Use Case | Statement | Private Input | Examples / Applications |
|---|---|---|---|
| Continuous Identity and Authentication | "I am authorised to use this service" | Identity | M-Pin |
| Supply Chain Security | "I am participant x" "Box x contains content y" |
Identity Content of Cargo |
OriginTrail |
| Internet of Things (IoT) device monitoring and control | "The device state of x is as expected" | Device state | Research Paper |
| Digital identity, authentication and signing of video/audio | "I am x" "I want to prove my signature" |
Identity Signature |
Set membership f(x)</td> </tr> |
| Secure code scanning | "The source code scanner completed scan X of code Y" | Source code | Verification of code scan |
| Vulnerability management | "Software x complies with security controls y" | Software code & configuration | Research Paper</td> </tr> |
| Intrusion detection and analysis machine learning and AI | "A baseline X has been interrupted by type Y" | Historical activity of systems in aggregate | Research Paper |
| Source code malware analysis with machine learning | "Source code x is free of known malware indicators" | Source code | BitAV</td> </tr> |
| Disaster Recovery and Data Redundancy | "We have computed backups at date X and successfully transmitted them to site Y" "Operational procedure X was successfully tested at site Y with expected outcome Z" |
Data | IBM Cloud</td> </tr> |
| Digital forensics | "Hash X was computed using library Y" | Confidential data | Research Paper</td> </tr> |
| Change management & auditing, FIM | "Approved Change X was deployed using procedure Y with integrity" | Yes Historical valid file changes |
zkledger |
| Smart contract security | "smart contract x follows security requirement y" | Smart Contract | aztec protocol |
| Secure continuous delivery assurance | "Item x has been processed at location y" | Location y | Chronicled</td> </tr> |
| Asset discovery and scanning | "Network discovery scan Y completed successfully" | Private IP ranges | Computation verification |
| Transparency in donations and funding | "Agency accepted donation amount x from entity y, x is within the approved donation range, y is on the list of approved donors" | Amount x, Entity y | Research Paper</td> </tr> |
| Non-profit agency spending | "Agency spent money on x, and x is within the set of approved expenses" | Expense x | Research paper</td> </tr> |
| Assurance of expenditures | "I've spend amount x on expense y" | Amount x | Nonprofit Assurance</td> </tr> |
| Asset tracking | "The location of asset x is y" | Location | Stratumn, Platin |
| Account takeovers mitigation | I am the authorised person to access account x | identity | Sovrin |
| Personal document assurance | "My passport number is y" | Passport information | IBM Blockchain Platform |
| Qualifications and education assurance | "I have qualification x" "I have a MSc degree in y" |
Qualification certificate | TiiQu</td> </tr> |
| Licensing assurance | "I have license x" | Licence certificate | Chronicled</td> </tr> |
| Medical record integrity and trust | "Patient x has disease y" | Patient record | Iryo</td> </tr> |
| Assurance of compliance and best practices | "Process x has been computed following y steps" | Y steps | Healthcare compliance</td> </tr> |
| KYC, AML, anti-fraud | "I am person x" | identity | ING, Sphere |
| Polling of electorate (referendums, elections) | "Votes x1...xn sum to y" | votes x1...xn | Stratumn |
| Direct politics | "Person X does not exist within voting set Y" | Person x | Set membership</td> </tr> |
| Transparency of spending and allocation | "We've spend amount x on y" | amount x | Government transparency</td> </tr> |
| Proof of process | "Y is the result of executing process x" | process x | Government transparency</td> </tr> |
| Tax | "For item x I've paid y tax" | Item x, tax amount y | QED-it |
| Equality of application of law | "Case x and y result in charge z" | Cases x and y | Book</td> </tr> |
| Verification of data with privacy | "Y is the result of f(x)" | data input x | QED-it |
| Chain of Custody | "Party X transferred item y to Party Z" | Item y | Chronicled |
| Integrity of evidence | "Evidence x has not been altered" | Evidence | Stratumn |
| Presence of suspect in database | "Suspect X has not had a record in Database Y before" | Evidence | ING |